Tyler is the one
task
Tyler has an incredibly busy schedule.
Government agents are after him for being too alpha, disrupting the
balance of alpha and beta energy of the world. He is trying to send a
secret message but we can’t decipher it. Here is the last trace he left.
Author: loltyler1dotcom-discount-code-alpha
Tags: file
writeup
let’s grab the file
1
2
3
4
5
6
7
8
9
10
11
| wget https://acmcyber.com/static/files/abde20916e91ef4d/alpha.jpg
--2022-11-18 16:57:25-- https://acmcyber.com/static/files/abde20916e91ef4d/alpha.jpg
Resolving acmcyber.com (acmcyber.com)... 54.215.8.184
Connecting to acmcyber.com (acmcyber.com)|54.215.8.184|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3880139 (3.7M) [image/jpeg]
Saving to: ‘alpha.jpg’
alpha.jpg 100%[==================================>] 3.70M 626KB/s in 7.1s
2022-11-18 16:57:33 (536 KB/s) - ‘alpha.jpg’ saved [3880139/3880139]
|
Here is the image:

Let’s check if this is really a jpeg file:
1
2
3
| file alpha.jpg
alpha.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, progressive, precision 8, 1920x1080, components 3
|
Nothing suspicious here.
Since this is a jpeg file I can check for any steganography using stegdetect
1
2
3
| stegdetect ./alpha.jpg
./alpha.jpg : appended(3741)<[nonrandom][data][PK........t.mU3=]>
|
according to stegdetect there are characters added.
We can try to extract data from it using steghide
1
2
3
4
| steghide extract -sf alpha.jpg
Enter passphrase:
steghide: could not extract any data with that passphrase!
|
But we don’t have a password.
However we can also use binwalk to extract data from this image.
1
2
3
4
5
6
7
8
9
| binwalk -e --dd='.*' alpha.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
246115 0x3C163 Zip archive data, at least v1.0 to extract, compressed size: 1978455, uncompressed size: 1978455, name: hidden.zip
2224616 0x21F1E8 End of Zip archive, footer length: 22
2224638 0x21F1FE Zip archive data, at least v2.0 to extract, compressed size: 1655251, uncompressed size: 1661078, name: tyler1.png
3880117 0x3B34B5 End of Zip archive, footer length: 22
|
Binwalk was able to extract two files: hidden.zip and tyler1.png.
We can’t extract hidden.zip yet because we don’t have a password for it.
1
2
3
4
| unzip hidden.zip
Archive: hidden.zip
[hidden.zip] secret.png password:
|
tyler1.png is a PNG file.
1
2
3
| file tyler1.png
tyler1.png: PNG image data, 1200 x 1600, 8-bit/color RGBA, non-interlaced
|
We can use a tool like zsteg or binwalk to find any hidden data in it.
1
2
3
4
5
6
7
8
9
| zsteg ./tyler1.png
b1,r,msb,xy .. file: OpenPGP Public Key
b1,b,lsb,xy .. file: OpenPGP Secret Key
b1,rgb,lsb,xy .. text: "r0fLM@OT1okg00dy3s"
b1,abgr,msb,xy .. file: PGP Secret Sub-key -
b4,r,lsb,xy .. file: Novell LANalyzer capture file
b4,g,lsb,xy .. file: 0420 Alliant virtual executable not stripped
b4,b,lsb,xy .. file: Targa image data - Map (256-256) 17 x 273 x 16 +257 +256 - 1-bit alpha "\001"
|
zsteg found something in the LSB (Least Significant Bit) which looks like a passphrase.
This could be the password for the hidden.zip file.
Let’s try to extract it with that password:
1
2
3
4
| unzip -P r0fLM@OT1okg00dy3s hidden.zip
Archive: hidden.zip
inflating: secret.png
|
Ok that was the correct password and we get a new file: secret.png
Let’s check the png file using the file command:
1
2
3
| file secret.png
secret.png: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced
|
Ok it is a png file.
Here is the image:

We can try to use binwalk again to see if anything is hidden in the file:
1
2
3
4
5
6
| binwalk -e --dd='.*' secret.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1920 x 1080, 8-bit/color RGBA, non-interlaced
54 0x36 Zlib compressed data, compressed
|
But there is nothing in there. Then I quickly scanned the file with strings to extract any printable characters but there is also nothing hidden.
If all of this does not lead to anything, we can use a tool like stegsolve to shift through the different color channels in the image to eventually find anything hidden in there.
Using stegsolve I am able to manipulate the colors. When given certain filters, colors that were barely perceptible before are made obvious.
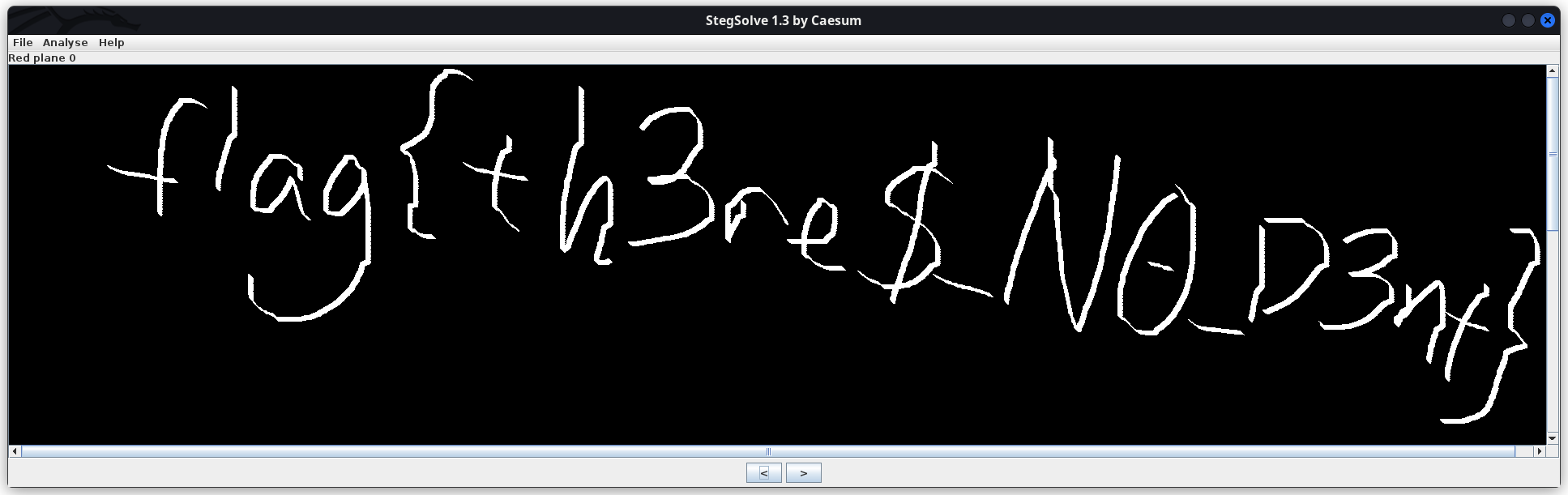
After shifting through the different color planes in stegsolve, I found the flag in the Red plane 0
Here is the flag visible:

flag: flag{th3re$_N0_D3nt}