Missing Person
task
I was zipping all my stuff together and realized that I’m missing a person. Could you find them for me?
Author: Luke
Tags: file
writeup
We get a file called stuff.zip.
And if we check the file signature using the file command, we can see that it looks like a regular zip archive.
1
2
| file stuff.zip
stuff.zip: Zip archive data, at least v2.0 to extract, compression method=deflate
|
Let’s extract this!
1
2
3
4
5
| unzip stuff.zip
Archive: stuff.zip
inflating: whygod.jpg
inflating: banana.jpg
inflating: stash2.jpg
|
Ok, we get 3 files: whygod.jpg banana.jpg and stash2.jpg.
Here are the files:



However all those files seem to be useless.
But there are only those 3 files, right? Wrong!
There are hidden files inside this zipfile which can be extracted using tools like cyberchef or binwalk.
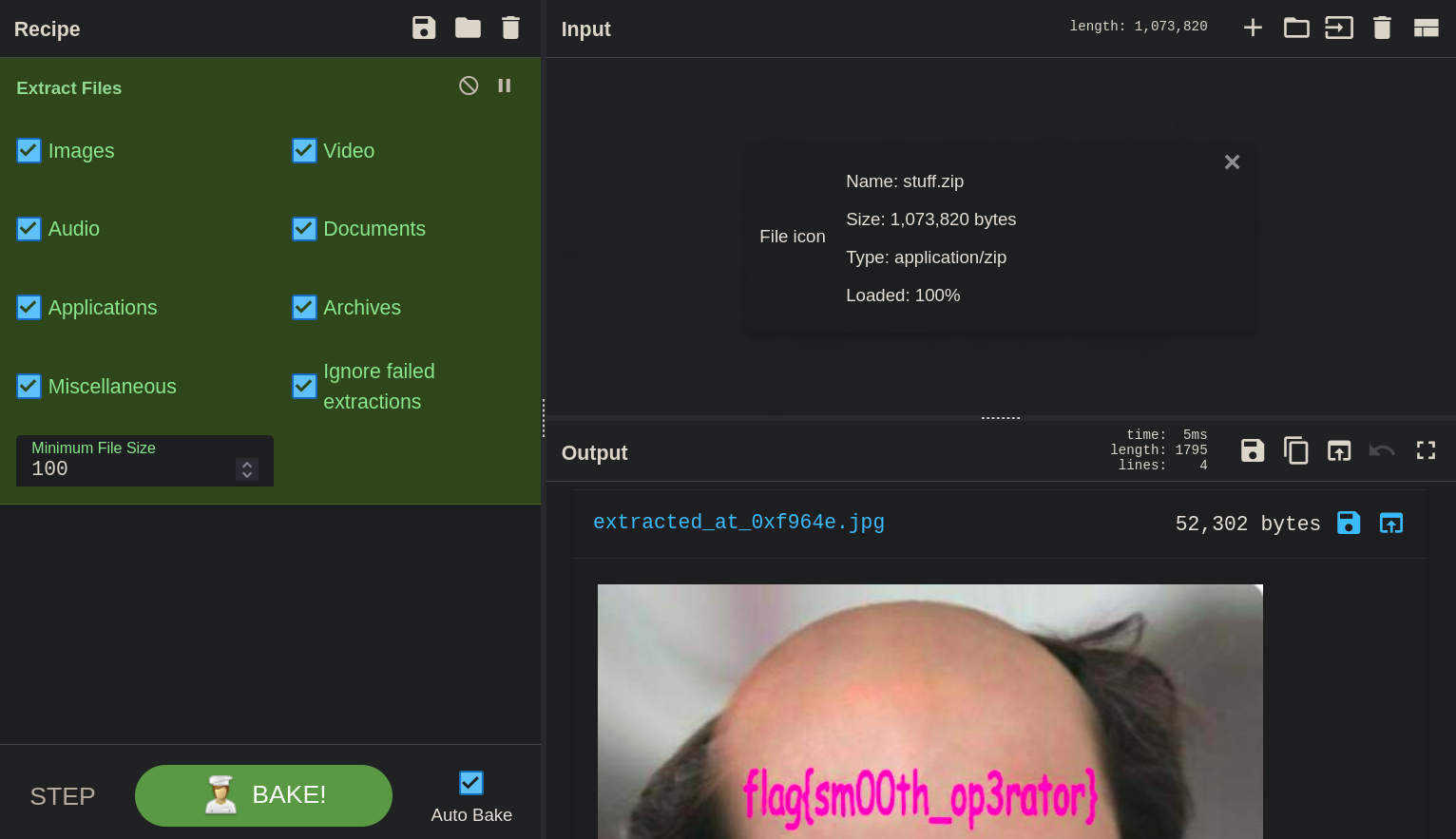
In fact we can use the Extract Files recipe of CyberChef to get the hidden file:

We can also get this file using binwalk.
We can use binwalk like so
1
2
3
4
5
6
7
8
9
10
11
12
| binwalk -e --dd='.*' stuff.zip
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 Zip archive data, at least v2.0 to extract, compressed size: 160689, uncompressed size: 160664, name: whygod.jpg
160729 0x273D9 Zip archive data, at least v2.0 to extract, compressed size: 131231, uncompressed size: 131862, name: banana.jpg
292000 0x474A0 Zip archive data, at least v2.0 to extract, compressed size: 729180, uncompressed size: 729476, name: stash2.jpg
1021496 0xF9638 End of Zip archive, footer length: 22
1021518 0xF964E JPEG image data, EXIF standard
1021530 0xF965A TIFF image data, big-endian, offset of first image directory: 8
1022232 0xF9918 Copyright string: "Copyright (c) 1998 Hewlett-Packard Company"
1032776 0xFC248 Copyright string: "Copyright (c) 1998 Hewlett-Packard Company"
|
1
2
3
4
5
6
7
8
9
10
| file *
0.zip: Zip archive data, at least v2.0 to extract, compression method=deflate
banana.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, Exif Standard: [TIFF image data, big-endian, direntries=4, software=Picasa, datetime=2020:04:25 10:07:27], baseline, precision 8, 774x811, components 3
F964E: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=9, height=828, orientation=upper-left, xresolution=122, yresolution=130, resolutionunit=2, software=Adobe Photoshop CS6 (Windows), datetime=2022:11:14 16:57:58, width=585], progressive, precision 8, 525x668, components 3
F965A: TIFF image data, big-endian, direntries=9, height=828, orientation=upper-left, xresolution=122, yresolution=130, resolutionunit=2, software=Adobe Photoshop CS6 (Windows), datetime=2022:11:14 16:57:58, width=585
F9638: Zip archive data (empty)
F9918: data
FC248: data
stash2.jpg: PNG image data, 741 x 758, 8-bit/color RGB, non-interlaced
whygod.jpg: PNG image data, 408 x 331, 8-bit/color RGB, non-interlaced
|
The new file here that binwalk extracted is F964E
1
2
| file F964E
F964E: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=9, height=828, orientation=upper-left, xresolution=122, yresolution=130, resolutionunit=2, software=Adobe Photoshop CS6 (Windows), datetime=2022:11:14 16:57:58, width=585], progressive, precision 8, 525x668, components 3
|
It is a jpeg file.
Here is the new image:

We can see the flag now!
flag: flag{sm00th_op3rator}